Suddenly, I was feeling the urge to browse for new wallpapers, sticking with my usual black series, with some areas colored in, and the desktop needing to display icons. Other color schemes would result in blurry icons.
I stared at the assembly code, trying to figure it out, but couldn’t understand it. I tried throwing it to an AI, explaining the instructions, but it failed to explain the context – clearly, this was a command used for a specific scenario. Regular code isn’t like that.
The AI was no longer as useful as a search engine at this point; its knowledge base of assembly language was insufficient.
Wallpaper
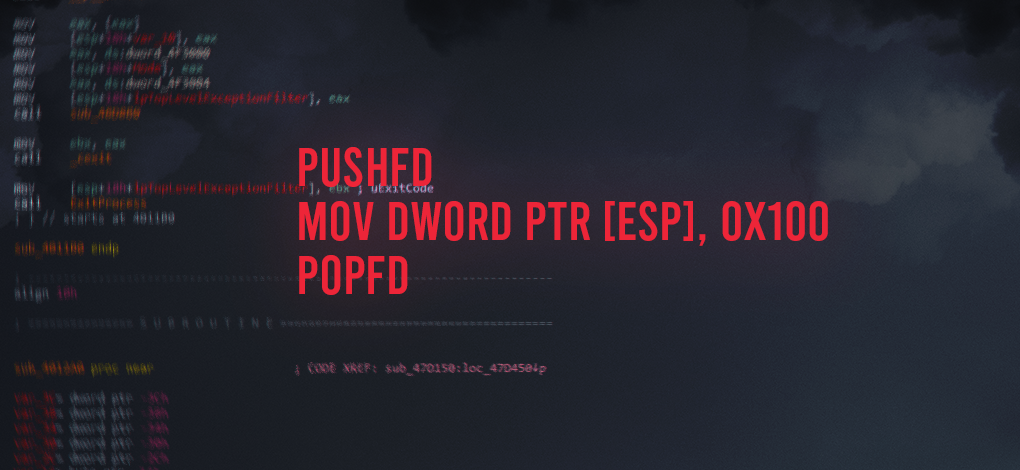
Assembly Code
PUSHFD
MOV DWORD PTR [ESP],0X100
POPFD
Actual Application Scenario
bool IsDebugged()
{
__try
{
__asm
{
pushfd
mov dword ptr [esp], 0x100
popfd
nop
}
return true;
}
__except(GetExceptionCode() == EXCEPTION_SINGLE_STEP
? EXCEPTION_EXECUTE_HANDLER
: EXCEPTION_CONTINUE_EXECUTION)
{
return false;
}
}
Explanation
TrapFlag is a flag bit in the register file. When this flag is set, it throws an exception SINGLE_STEP. Because when we trace the code, this flag will be cleared by the debugger, so we won’t see this exception.
In actual testing, if you directly step over detecting functions, debugging will not be detected. Only when entering the detection function to execute will it be detected (based on research materials, yet to be verified in practice).
References
Chinese related materials are based on the English articles from websites, which introduce many anti-debugging techniques.
- https://anti-debug.checkpoint.com/ techniques/assembly.html
- https://song-10.gitee.io/2021/08/08/Reverse-2021-08-08-anti-debug/